I have a story to tell you: it is set in a backyard BBQ on the fourth of July, or a family gathering, or the break room at the office. Regardless of the setting, the characters are all (mostly) the same: an enthusiastic cyber security professional (let’s called them “CSP” for short) and literally anyone else (we’ll call them “John”). The story unfolds when that other person inevitably asks the cyber security professional, “so, what do you do for a living?”
It is at this point that the story can diverge. The first story path has CSP diving into the specifics of his or her job and John’s face glazing over from an assault of acronyms, bizarre names, and other extraneous information. The second path — the one that seems to be the default choice for many veterans of the cyber security field — is to say: “I’m in I.T.” Upon hearing that description John may prod for more information, but almost invariably once you get into the nitty gritty of cyber security (let alone your speciality) John is back to having a glassy look to his eyes.
This is a story that plays out far too frequently, in my opinion. And as someone who has been CSP time and again, I wanted to put together a resource that might help the uninitiated to understanding what a threat hunter actually does.

Before Me, There is You (and Your Logs)
Before we get started, however, I want to talk about you. (Yes, you!). You are one of the individuals that are entrusted day-to-day to not only get your job done but also to keep the company safe. Didn’t know that, huh?
Well, whether you work in finance, legal, or any other department, you have an important role to play in the security of a company. Whether it be from malicious documents that you don’t open and report in or USBs that you found on the ground and turn in to security, your contributions matter a lot to the security of a company. But, did you also know that you play another important role in the security process?
You may not know it, but everything you do on your work computer is logged, and it helps to paint a picture of your daily routine, and what is considered normal for you. This daily routine can help cyber security professionals during investigations, and can help identify anomalies in activity.
What Are You Doing to Help
Let’s get down to how you are helping fight the good fight!
When you carry out most any activity on your work laptop, something called an “Event Log” is generated. These Event Logs record important activities, such as logging in, changing your password, or even opening a program.
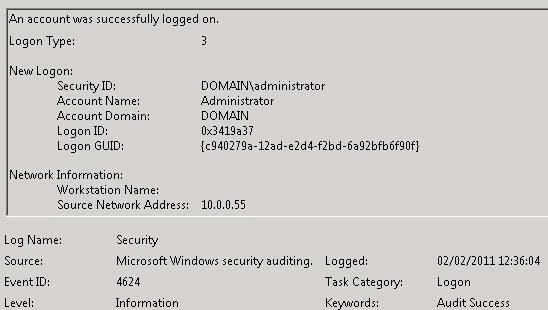
For instance, on Monday morning when you go to log in to your workstation, that action is recorded as good old Event ID 4624 (successful login) or maybe Event ID 4625 (failed login) if you changed your password on Friday and you forgot it over the weekend, but no matter.
Some of the information that can be gathered from this log is that you logged in with your username, what time it was, and what workstation you are at, physical (at your desk) or logical (such as logging into a remote desktop session).
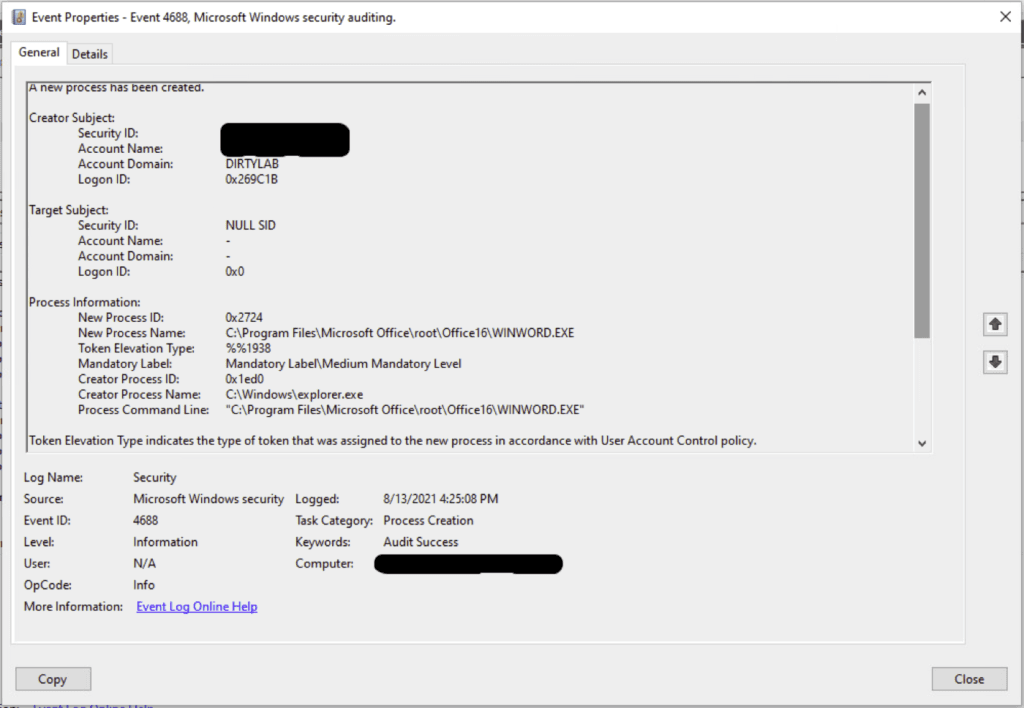
Now after logging in on Monday morning (or resetting your password… again!), the first thing that needs to be done is catch up on your work emails that people sent you over the weekend. So, you open your email program – Event ID 4688 (a process has been created). Again, important information can be collected from this log: What user created the process, what the parent process was (the process name that kicks off the process), and the child process (the process being opened). All this information is helpful in identifying what is normal vs abnormal.
How Do We Look at Event Logs
One thing to mention about the Event IDs: these occur locally on your computer and can be viewed using a tool called Event Viewer (if you have the proper permissions). There is a technology that takes these events from your local device and ships them across the network to a tool called a Security Information and Event Manager, or SIEM. This is a form of centralized logging and allows cyber security professionals to compare logs and hunt for abnormalities. What this means is that analysts don’t have access to your computer and files, but instead are viewing the logs that are generated because they were shipped to a central location.
Parent-Child Process Relationship in the Logs
Let’s take a quick look at what I mean by parent process and child process. If a user navigates through the Windows Start Menu or from a shortcut to start Microsoft Word for example (WinWord.exe), the parent process should be explorer.exe, which is the executable in Windows that “contains the Start menu, Taskbar, desktop and file manager.” Therefore, normal, user-driven, activity would look like is this:
User = You
Parent process = explorer.exe
Child process = WinWord.exe
But how do we determine normal vs abnormal parent-child processes?
Normal vs Abnormal Event Logs
Now the two (or three) Event IDs I mentioned above, it would be hard to conclude anything but what those Event IDs can provide is a good start for building an assessment of what is normal. Let’s say that every day you log into the same workstation at 8am (or 8:15 if the line at the coffee shop is really long!) and this has happened every day since you started – this establishes a baseline behavior. Now, let’s say that you got a new laptop from work to replace your old one, and you logged into it for the first time at 9pm at night on a Saturday. This might raise some suspicion or even an alert, and a CSP would likely identify this as an anomaly and an investigation would ensue – though it would be eventually closed off, as your behavior otherwise seems unsuspicious, or normal.
However, let’s say that your account was observed connecting to a server or other device you don’t typically connect to – regardless of the time or day that you connect. That is immediately cause for concern, and this would likely trigger a series of events as the activity is highly abnormal.
The Hunt! (The Fun Part)
The job of a threat hunter is to examine these behaviors — and indeed, many more complex ones — to identify suspicious activity. They do this by carrying out “hunts” where they identify a specific behavior to see if it has occurred across the network, what they did, and then respond to it.
There are a couple of ways to go with the hunt, but I want to show you one way to start using the Event IDs that I mentioned earlier.
The first point would be the username for the abnormal log in to the server I mentioned. Knowing that the account was possibly compromised, we would look for more abnormal activity with the intention of finding the beginning of the suspicious activity and perhaps the cause of the infection.
An example of what this “cause” could look like – note, we will be using Boolean Logic here – would be something like
Username = You AND
Parent process = Outlook.exe AND
Child process = WinWord.exe
Now, this activity in-and-of-itself wouldn’t be either suspicious or malicious. In fact, this is behavior that occurs every time you open an attachment in Outlook! However, if that child process then becomes a parent (they grow up so fast!) process and spawns something like PowerShell, that would be cause for serious concern.
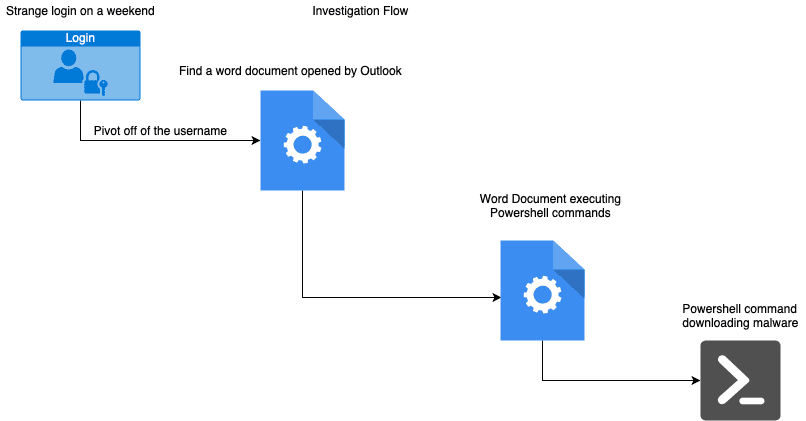
As a pretty reliable rule of thumb, Microsoft Word should not be spawning PowerShell because Word is a word processor, not a program launcher. However, there are things that can be created called “macros” that will enable Word to complete tasks that is written for it. PowerShell is a powerful tool that is used by administrators for legitimate reasons but is also targeted by malicious actors as well for nefarious reasons. They can use PowerShell to reach out to the internet and download malware onto your workstation or change configurations that will make the workstation less secure.
If a threat hunter observed this type of activity, it would likely be flagged for follow up investigation and remediation.
Conclusion
Cyber security can often be a complex topic, even at the best of times. And explaining to someone what threat hunting is can often cause more questions and confusion than it solves. But, by connecting the dots for the average user and demonstrating to them how their individual activities can influence the security investigation process, I hope to avoid the glassy-eyed look of John (or anyone else!) and help others understand what the day in the life of a cyber security investigation looks like!